ALEXANDRIA, Va. — Imagine deploying a GPS receiver on the International Space Station (ISS) to study the Earth’s atmosphere and discovering a way to geolocate and characterize illegal jamming and spoofing signals.
 The Global Positioning System (GPS) is a U.S.-controlled constellation of orbiting satellites that provides position, navigation and timing data to military and civilian users globally. Global Navigation Satellite Systems (GNSS) generally satellites constellation with that capability. (Source: USSF)
The Global Positioning System (GPS) is a U.S.-controlled constellation of orbiting satellites that provides position, navigation and timing data to military and civilian users globally. Global Navigation Satellite Systems (GNSS) generally satellites constellation with that capability. (Source: USSF)
That’s what happened to Todd Humphreys, professor of aerospace engineering at the University of Texas at Austin’s Cockrell School of Engineering. Humphreys is an authority on radionavigation and author of the most cited paper on GNSS spoofing. Over the last five years, he and a team of researchers engaged in an experiment that caught the attention of the military and private industry for its potential impact on the future of electronic warfare.
A Lucky Break
In 2017, Humphreys had the opportunity to deploy an experimental, software-defined multi-frequency GNSS receiver onboard the ISS as part of a GPS radio occultation study of the atmosphere and ionosphere. The experiment was done in partnership with Cornell University and the Naval Research Laboratory. A short time after deploying the receiver, he became aware of a pattern of widespread GPS spoofing in the Black Sea through his work with a global security nonprofit, the Center for Advanced Defense Studies (C4ADS).
“As we looked into this further, we recognized the spoofing was always following the same pattern. It would take ships on the Russian side of the Black Sea and they would be spoofed to locations near airports,” Humphreys told Constellations.
Ships would appear in an entirely different location on their automatic identification systems (AIS) and would be perceived to be in the spoofed location by other vessels. In at least one case, a ship in the northern Black Sea was spoofed to Moscow.
Because the false signals were being broadcast in the same L1 (1575.42 MHz) and L2 (1227.60 MHz) bands utilized by GPS satellites, it occurred to Humphreys that they could be picked up by the experimental receiver. If the signal was strong enough and it was recorded at the right time, it could reveal the location of the disruption.
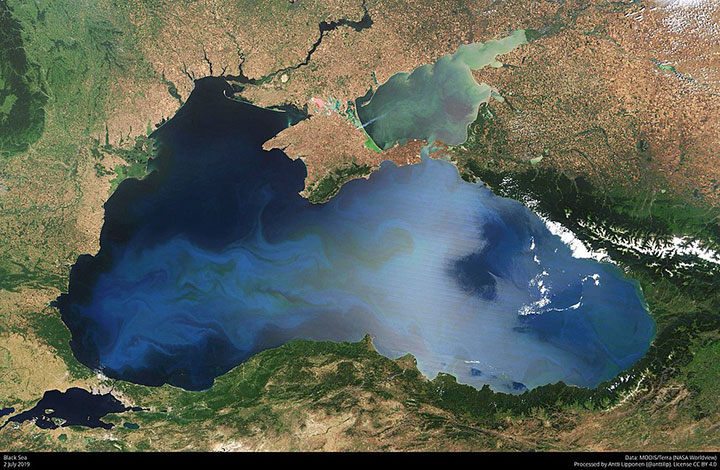 This 2019 satellite image shows the Black Sea. Ships navigating the Russian-controlled waters of the Black Sea are subject to regular GNSS spoofing and interference. (Source: NASA)
This 2019 satellite image shows the Black Sea. Ships navigating the Russian-controlled waters of the Black Sea are subject to regular GNSS spoofing and interference. (Source: NASA)
A special feature of the experimental receiver was its ability to record raw signals data. Also, because it was software-defined, it could explore different signals with a code update. Over several days, the team recorded a few satellite passes. Using Doppler-based methods, they confirmed the location of the signal: Syria.
“The signals in the Black Sea were there, but they were eclipsed by a much stronger signal, also from a Russian transmitter, but located in Syria,” Humphreys explained.
In this particular incident, the disruptions initially looked like spoofing, but turned out to be matched-code jamming. This is a potent form of jamming where the false signal closely simulates GPS spreading code but, in this case, lacked navigation bit modulation.
Fast forward to April 2022. Humphreys and his team again had their experimental receiver trained on a location in the eastern Mediterranean. This time, the receiver captured a signal that had the GPS spreading code plus the additional navigational features needed to fool a GPS receiver.
“For the first time in the wild, we had a recording of a full-blown spoofing signal,” Humphreys said.
Laying the Groundwork for Commercial and Defense Adoption
Through the experiment, Humphreys and his colleagues became the first to show that a low Earth orbit GNSS receiver could be used to geolocate the source of terrestrial spoofing and jamming and characterize the false signals.
The proof attracted attention from satellite operators who recognized the potential military and commercial applications of the technology and estimation algorithms.
“That’s the way we think of our job as academics. We prove the concept, we explain how it can be done and then let a thousand flowers bloom, let other people run with it,” Humphreys said.
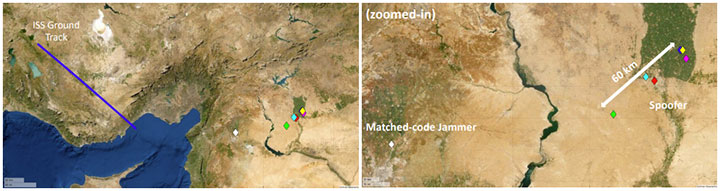 This image from Todd Humphrey’s 2022 paper on geolocation of terrestrial GNSS spoofing signals shows how the Doppler time histories of a single matched-code jammer signals and six spoofing signals were used to estimate a transmitter position with less than 100 km accuracy. The white marker corresponds to the matched-code jammer and the colored markers correspond to the spoofing signals. (Source: Todd Humphreys/UT Texas Radionavigation Laboratory)
This image from Todd Humphrey’s 2022 paper on geolocation of terrestrial GNSS spoofing signals shows how the Doppler time histories of a single matched-code jammer signals and six spoofing signals were used to estimate a transmitter position with less than 100 km accuracy. The white marker corresponds to the matched-code jammer and the colored markers correspond to the spoofing signals. (Source: Todd Humphreys/UT Texas Radionavigation Laboratory)
Currently, Spire Global and HawkEye360 are using the proof in developing platforms capable of detecting and geolocating terrestrial GPS interference. Other organizations have shown interest as well.
The experiment resonated in the national security community. Incidents of intentional GPS interference have been rising in recent years as the cost of spoofers and jammers decreases and availability increases.
Numerous accounts of spoofing by state and non-state actors have been documented in both wartime and peacetime scenarios. Used peacetime, the GPS interference can erode trust in navigation systems across domains. So far, its effects have been inconvenient and mostly limited to economic disruptions, but it could potentially impact navigational safety.
Spoofing, as distinct from jamming, deceives receivers and typically serves as a defensive tactic or cover illegal activities, such as sanctions evasion. GPS jamming, which denies service by emitting signals in the frequencies used by GPS, has been a regular feature of modern warfare.
Nowhere to Hide from Multiple Satellites
Humphreys acknowledged he got lucky in detecting the jamming and spoofing signals. Had the false signals been weaker or the transmitter clocks less accurate, it would have been difficult if not impossible to geolocate with precision.
The single biggest limitation of the ISS experiment was the use of a single sensor on a single satellite. That’s where Spire comes into play. Spire is a global data and analytics company with a fleet of over 100 satellites in a variety of low Earth orbits. Humphreys and one of his students have been collaborating with the company on a multi-satellite, multi-receiver experiment using two Spire satellites to pinpoint sources of terrestrial GPS interference.
“If you have two or more satellites, there’s no place to hide,” Humphreys emphasized. “As long as the signal is strong enough, you’ll be found.”
The satellites’ location in low Earth orbits eliminates the effects of terrestrial interference, allowing accurate tracking of authentic GPS signals. Time-synchronized satellite receivers can detect the emitter’s location in a single step using time- and frequency-difference of arrival methods (TDoA and FDoA). Multiple satellites can be effective even if the signal is narrowband or wideband or the clock tone is poor. They can also locate a moving transmitter, which is much harder with a single satellite.
A Battlefield Liability
Militaries around the world are exploring ways to manage the growing use of GPS jamming and spoofing tactics. One option is to harden GPS receivers against interference. While effective, it’s still easier to jam than harden receivers, giving the adversary the asymmetric advantage.
 Accurate satellite-based geolocation can help detect battlefield spoofing and jamming threats. This Dec. 9, 2020, photo shows paratroopers from 2nd Brigade Combat Team, 82nd Airborne Division conducting a range exercise in NE Syria in support of Operation Inherent Resolve. (Source: U.S. Army/Spc. Sidney Perry)
Accurate satellite-based geolocation can help detect battlefield spoofing and jamming threats. This Dec. 9, 2020, photo shows paratroopers from 2nd Brigade Combat Team, 82nd Airborne Division conducting a range exercise in NE Syria in support of Operation Inherent Resolve. (Source: U.S. Army/Spc. Sidney Perry)
Another option is to use multiple satellites to precisely geolocate and target the source of interference in real-time. This would upend the advantages of battlefield spoofing and jamming, making those who engaged in it a liability.
The irony of using signal jammers in a conflict is they have to generate a lot of power to be effective, Humphreys noted. “If it’s loud, you can find it quite quickly—if you have enough space assets.”
This could potentially change the dynamics of electronic warfare moving forward. A large enough constellation outfitted with GPS receivers could provide persistent monitoring for disruptive signals. Satellites could deliver precise geolocation data to artillery units on the ground, which could eliminate the source of GPS jamming.
Humphreys noted that the experiment was designed for a standard science experiment, but opportunity and curiosity intervened.
The U.S. government has demonstrated interest in capabilities that shorten the cycle of locating jammers and putting targets on them. The Department of Defense has agreements with both Spire and HawkEye360 for signals monitoring from space.
Explore More:
Podcast: Maj. Gen. Bratton on STARCOM and Virtualized Training for Space
Podcast: SDA Technical Director on Spiral Development, Technology Readiness Levels
Podcast: The Difficulty of Servicing Spacecraft, Navigating without GPS and Space IoT
