
Since the onset of the Russia and Ukraine War in March 2022, there has been a sharp increase in retaliatory cyberattacks conducted by numerous pro-Russian and Ukrainian cyber groups. Following the initial string of data wiper attacks from Russia, analysts have identified a loose coalition of hacktivists joining the battle by defacing public websites, infiltrating servers and leaking sensitive information on dark web forums. In addition to wiper attacks and the use of worms to infiltrate networks and exfiltrate data, there has been an expanded footprint of cyber hacktivist groups that have taken sides in the war.
This activity began, in large part, due to the Anonymous cyber collective, who began to deface Russian websites, hack email servers and leak information at the onset of the invasion. This was soon followed by retaliatory attacks from pro-Russian cyber groups looking to inflict damage on Ukraine and its supporters. The predominant hacktivist group is tracked as “Killnet,” which is a virulently pro-Russian cyber collective, focused on disrupting assets natively in Ukraine and organizations directly supporting their war efforts.
Killnet is characterized by researchers at Avertium as “a pro-Kremlin hacker group known for targeting European governments and infrastructure via disinformation campaigns.” Killnet often communicates on Telegram, utilizing the platform to both plan attacks as well as to claim responsibility for successful ones. Analysts have been closely monitoring these Telegram channels and have seen that Killnet has claimed direct responsibility for attacks on aerospace firms. Over the last six months, Space ISAC has tracked seven separate examples of the hacktivist group directly targeting aerospace organizations by disrupting public-facing assets such as websites and user platforms.
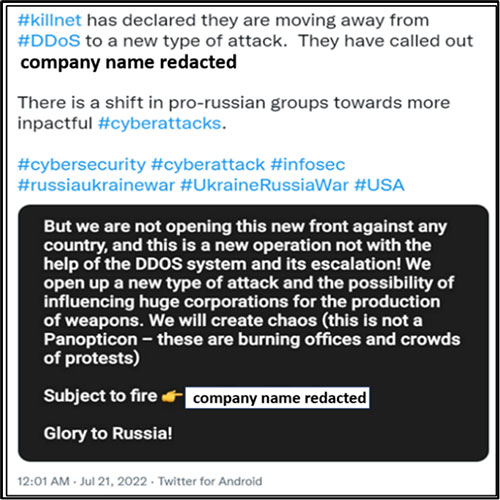 Figure 1: Killnet claims cyberattack on US Aerospace Firm (company name redacted for privacy)
Figure 1: Killnet claims cyberattack on US Aerospace Firm (company name redacted for privacy)
These incidents have ranged from brief outages to IT assets, such as the White House website and Starlink’s broadband service platform, to coordinated disruptions to government networks in Lithuania, affecting both public and private infrastructure. According to researchers at Forescout, Killnet’s go-to attack vector has been Distributed Denial of Service (DDoS) attacks, leveraging brute-force to harvest credentials on TCP ports, and SSH tunneling to carry out attacks.
These attacks have targeted critical infrastructure entities, airport websites, government services, U.S. based defense firms and media companies within NATO countries, including the U.S., Canada, Australia, Italy and Poland. Killnet has also targeted Ukrainian supporters in practically all Eastern European, Nordic and the Baltic countries.
Killnet’s self-proclaimed anti-war mandate alleges that their primary targets are supporters of Ukraine, including NATO countries and their allies. Despite the group’s relative lack of sophistication, Killnet is nonetheless considered a credible threat to critical infrastructure, as well as aerospace firms who are perceived as aiding Ukraine. Killnet was prominently mentioned in a multi-national joint cybersecurity advisory, dated April 20, 2022, in relation to a DDoS attack against a U.S. airport.
While the impacts of Killnet’s activity have been less than devastating, the group has nonetheless demonstrated an affinity toward targeting US based aerospace firms with disruptive DDOS attacks and thus poses a real threat. A well-timed DDOS attack can be damaging to satellite operations as well as cause user turmoil. Firms with less mature cybersecurity capabilities and incident response plans may find it strenuous to recover from an attack of this nature. As tensions continue in Ukraine, it is likely that hacktivist groups will continue to inflict damage on a variety of industries perceived as supporting war efforts.
Read more from Space ISAC.
