
Executive Summary
Over the last 18 months, cyberattacks on space networks have become more common. Threat actors are demonstrating intent to deny supporting critical infrastructure via exploitation of vulnerabilities present in space networks. Space operators and security professionals alike are aware of the vulnerabilities posed to ground-based architecture, including satellite terminals that can be exploited by a variety of cyberattacks. Such was the case in late June 2023, when hackers associated with the PMC Wagner group claimed responsibility for a cyberattack on Dozor-Teleport. This attack represents the second major cyber incident affecting a satellite communications company; following the major disruption of a US satellite company in February 2022, when Viasat’s KA-sat was disrupted at the onset of the Russian invasion of Ukraine.
Overview
Dozor-Teleport is a Russian satellite telecommunications provider that serves various entities, including power lines, oil fields, Russian military units, Northern Fleet ships, a nuclear power plant and the Russian Federal Security Service (FSB). The group initially announced the attack on Telegram, and metrics indisputably show a disruption to Dozor’s satellite internet functions. In addition, Dozor’s parent company, Amtel Svyaz, was also targeted and suffered a significant outage. The attack was confirmed by the hacking group, which posted a message on Telegram claiming responsibility for the attack and threatening that more attacks were coming. Included in the communication was a link to a zip file that contained nearly 700 files, preceding an additional data dump of files and passwords supposedly showing the company’s connection with the Russian Federal Security Service (FSB).
Analysts confirmed via the Internet Detection and Analysis Project (IODA) that the outage began at 2:00 am UTC, 29 June and persisted until 5:00 pm UTC, lasting nearly 15 hours. Additional analysis shows that Dozor-Teleport did not resume normal operations until approximately 1:30 am UTC on 7 July. While the full impact of the outage remains unclear, additional sourcing identifies that Dozor-Teleport (AS number 419412) has significant upstream connections, most notably the Joint Stock Company TransTeleCom and PJSC VimpelCom, two of the largest telecommunications companies in Russia.
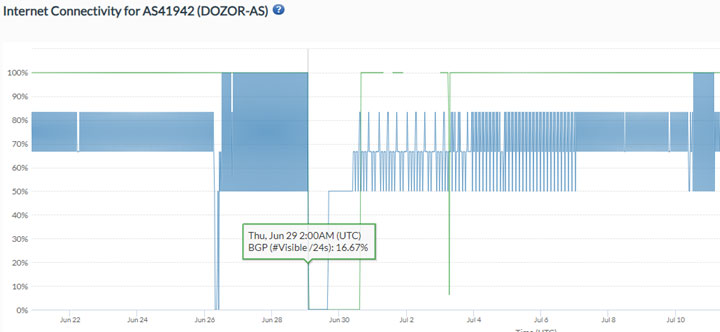 Figure 1: Dozor Outage Report, derived from IODA
Figure 1: Dozor Outage Report, derived from IODA
According to the message posted to the group’s Telegram channel, “Part of the satellite terminals failed, the switches rebooted, and the information on the servers was destroyed.” While the primary attack vector is still unknown, this information relays that the attack was successful. This is due in part to the satellite terminals, which have been known to be vulnerable to jamming attacks. More recently, terminals have been targeted by fault injection attacks precipitated by custom-built modchips, as reported in a 2022 Wired article mentioning techniques for hacking Starlink terminals. The significance of the Dozor-Teleport attack cannot be understated, as the disruption of satellite terminals can lead to widespread outages of dependent infrastructure.
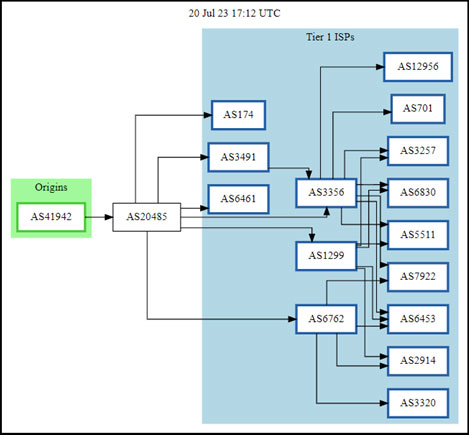 Figure 2: Connectivity of AS41942 (Dozor-Teleport) Derived from bgp.tools
Figure 2: Connectivity of AS41942 (Dozor-Teleport) Derived from bgp.tools
Read more from Space ISAC.
