 Figure 1: EXSiArgs Exploit Killchain. (Source: TrustedSec)
Figure 1: EXSiArgs Exploit Killchain. (Source: TrustedSec)
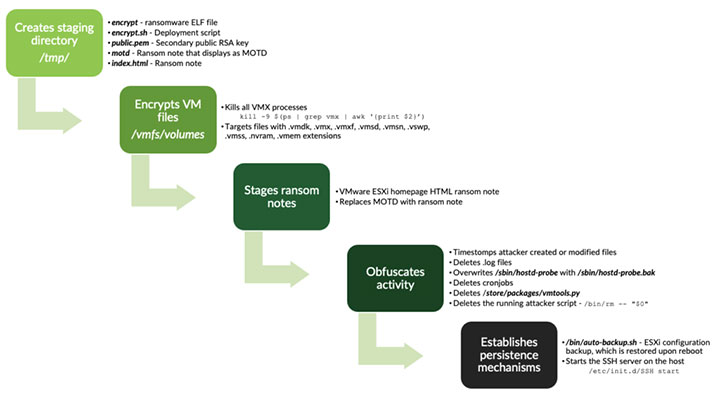
In early February, analysts identified that a previously patched vulnerability in VMware ESXi was being exploited to deliver ransomware files and malicious packages to ESXi servers. The exploit has affected organizations on a global scale and enables remote code execution (RCE), allowing attackers to issue malicious commands via remote connection. The vulnerability was exploited over the last two years, with an initial patch released in 2021. There has been a threefold increase in EXSI exploits since the release of the original patch, according to a report from Recorded. This suggests that the vulnerability was not adequately patched or that threat actors have engineered exploits to bypass this fix.
Virtualized environments are becoming increasingly common in space networks with uses including digital twin architectures, simulated test environments, software-defined radio and applications like C2 support. One such evolving capability is found in VM bolstering satellite communications. In 2022, MetTel Labs announced the deployment of software-defined wide area network service using the VMware SD-WAN solution over Space X’s Starlink satellite service.
Initial warnings of the exploit, known as ESXiArgs, came from the Cybersecurity and Infrastructure Security Agency (CISA) and other computer emergency response teams (CERT), stating that it was active in the wild as of February 3, 2023. It was so severe that CISA and the FBI released a recovery script on February 8 to help organizations recover encrypted files and patch the vulnerability. Since then, a new version of the malware has appeared that bypasses the script, and reports coming from security researchers and computer emergency response teams show a continuing growth in new server compromises.
Early estimates show that around 4,000 servers were compromised, followed by a further surge the following week. Additional estimates, provided by researchers at Rapid7, suggest upwards of 18,000 internet-facing servers are vulnerable to ESXiArgs as of February 9. Organizations continuing to use outdated or unpatched version of ESXi are at high risk of vulnerability exploits from the ransomware campaign.
Virtualization technology such as VMware is becoming a key component to the success and security of organizations across all major sectors. The benefits include the ability to operate different OS types so that multiple systems can be hosted on a single machine, with the most common application being server virtualization. This may be especially important for satellite operators that have to interface with, in some cases, decade-old legacy systems.
As the potential for virtualization technology supporting space systems continues, it is crucial that organizations stay abreast of patches, hotfixes and other updates released for exploits like ESXiArgs, just as they should with all other applications and operating systems. It is being reported with high confidence that the exploited VMware ESXI servers are running outdated OS versions. While there are multiple threat actors looking to exploit this vulnerability, patches exist, and organizations with vulnerable servers should look to update patching strategies and stay up to date with newly developed guidance published by vendors, CERTS and government agencies.
Read more from Space ISAC.
