
Overview
In May 2023, researchers from Thales successfully demonstrated how to hack into an orbiting satellite. During the recent European cybersecurity and space exhibition (CYSAT) held in Paris, France on April 26-27, the European Space Agency (ESA) set up a satellite test bench to simulate attempts to seize control of OPS-SAT, a nanosatellite operated by the agency for demonstration purposes. The demonstration was organized specifically to help determine the potential impact of a real cyberattack and the consequences for civilian systems. Among the participating teams were cybersecurity researchers from Thales, who managed to successfully command the nanosat using a “variety of ethical hacking techniques to take control of the system used to manage the payload’s global positioning system, attitude control system and onboard camera.”
While the purpose of this exercise was to demonstrate the art of the possible pertaining to on-orbit cyber operations, Space ISAC sees value in the outputs as informing members of the satellite community on the countermeasures and courses of action that can be taken to improve the resiliency of satellite systems. This experiment can be used as an example to dissect the various tactics, techniques and procedures that led to the compromise of OPS-SAT and identify appropriate countermeasures to defend against intrusion attempts.
From the Space ISAC’s perspective, an analysis of the attack pattern and intrusion set of the Thales team can enumerate how satellite owners can prepare for and respond to threats to their systems.
Attack Pattern Analysis
Researchers at ESA worked alongside exercise participants to provide system descriptions and capabilities that were necessary for exploits to take place. The OPS-SAT featured a Satellite Experimental Processing Platform (SEPP), a hosted payload designed to enable software deployment. Additionally, ESA provided the ethical hacking teams access to the Nanosat Mission Operations Framework (NMF), which was critical in the development of the OPS-SAT conops. Access to these capabilities comprises much of the reconnaissance and resource development requirements needed for a successful exploit of the satellite. If an adversary were to succeed in a similar campaign, these resources would need to be accounted for.
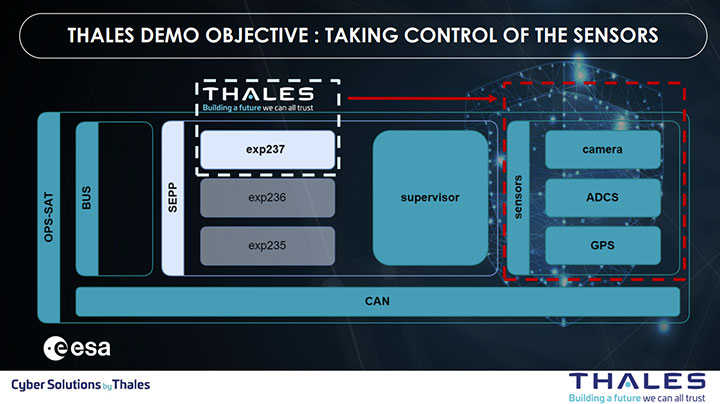
The Thales research team, acting as threat actors, sought to identify and exploit onboard vulnerabilities that could enable disruption of critical satellite mission operations. Their goals were to escalate privileges to take control of OPS-SAT’s various subsystems while staying undetected. The attackers were able to leverage their legitimate access (valid accounts) to deploy a third-party software application that concealed a malicious payload.
The Thales team successfully hacked into the satellite’s onboard system by using elevated access rights to obtain control of its application environment. After achieving access, the researchers were able to deploy malicious code into the satellite’s systems by exploiting system vulnerabilities. During the course of the designed attack sequence, the Thales group researchers identified vulnerabilities in OPS-SAT’s operating system that enabled disruption of the satellite’s flight software.
Through this exploitation, data sent by the satellite back to Earth was compromised. In particular, images captured by the satellite’s onboard camera were modified. Also, the research team was able to mask selected geographic areas in the satellite imagery while simultaneously concealing their activities to avoid detection by ESA.
Courses of Action and Countermeasures
The attack pattern analysis of this exercise allows analysts to identify the proper precautions and responses security teams may enact to prepare for and respond to real-world attacks. By correlating observed behaviors to tactics, techniques, and procedures included in the MITRE ATT&CK and Aerospace SPARTA frameworks, Space ISAC Analysts determined that the most relevant courses of action related to increased intrusion detection capabilities, vulnerability assessment, and network/device segmentation.
Intrusion Detection Systems (IDS) have long been an integral part of cyber defense and incident response; this capability is actively being integrated to spacecraft with onboard IDS software. This countermeasure would allow the victim to detect abnormal behavior and stop the attackers from escalating privileges.
In the case of the ESA OPS-SAT experiment, attackers exploited a deserialization vulnerability in the nanosat management framework (MDF). Proper risk assessment of this vulnerability could lead development teams to implement a patch or additional security measures to protect this vulnerability from being exploited in the first place.
Lastly, implementing network segmentation would reduce the ability for attackers to move laterally once initial access was achieved. In this scenario, segmentation would prevent attackers from gaining control of the SEPP subsystems and ultimately disabling operations.
Industry frameworks like MITRE ATT&CK and Aerospace SPARTA allow researchers to implement effective countermeasures, follow proven courses of action to prevent intrusion attempts, and severely limit the impact that cyber-attacks can have on victims, regardless if the network is ground or space-based. Designed, ethical hacks of satellite networks, as witnessed with the OPS-SAT experiment, can be a tremendous tool for analysis that will allow the satellite industry to prepare for future cyberattacks.
Read more from Space ISAC.
